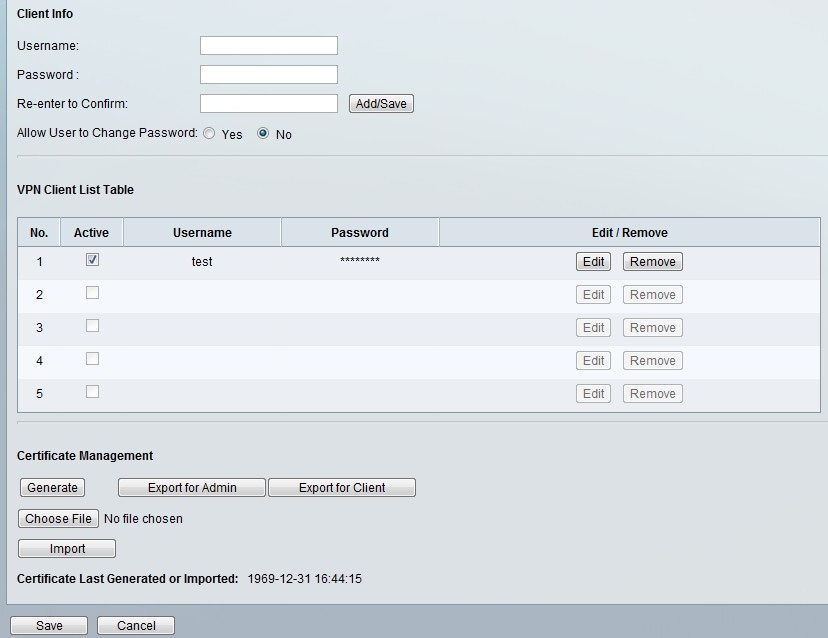
QuickVPN is an easy way to set up VPN software on your remote computer or laptop with a simple username and password. This will help you securely access networks based on your Small Business Router. QuickVPN software is compatible with Windows 7 operating system (32-bit and 64-bit editions), Windows XP (32-bit), and WIndows Vista (32-bit and 64-bit editions).
How to Use Cisco QuickVPN 1. Double-click the Cisco QuickVPN software icon on your Desktop or System Tray, or go to Start Programs Cisco Small Business QuickVPN Client. Enter a new Profile Name or select a saved profile from the drop-down list. When creating a new profile, enter the following information. According to Cisco support, QuickVPN connections to this device require that the inside interface of the router be set to a 10.x.x.1 address. Assuming that your LAN isn't 10.x.x.1 this would mean a readdressing of all devices, DNS changes, etc.
Company Size
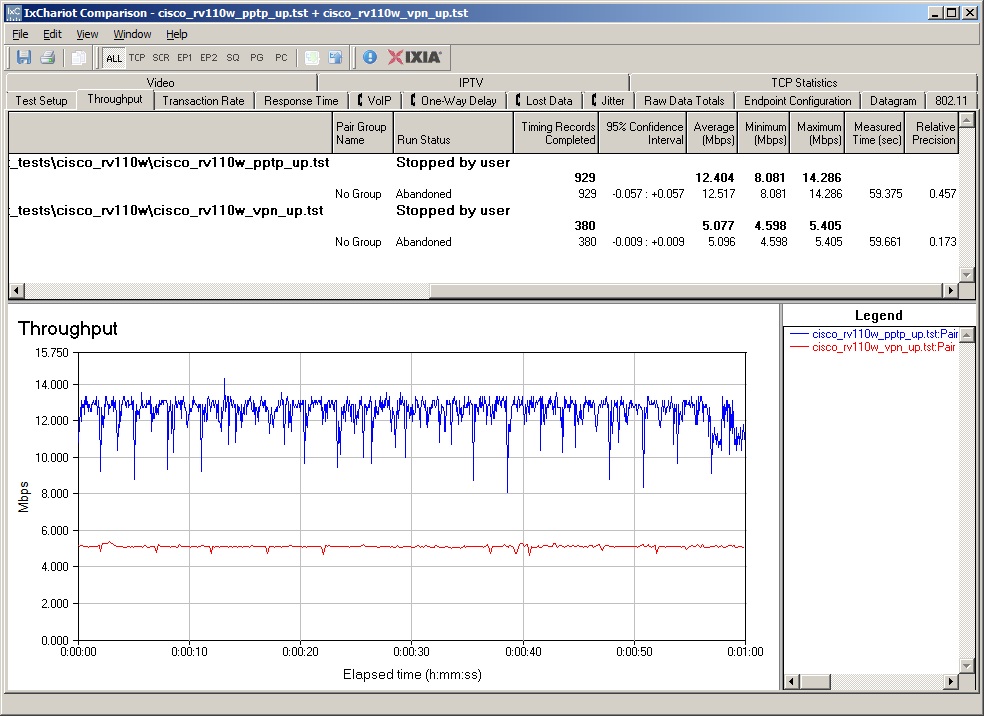
Cisco Quickvpn Client Failed To Establish A Connection

Cisco Quickvpn Download
- S
- M
- L
IT Pro Reviews of Cisco Systems, Inc QuickVPN Client
- Access Control Management
- Advanced Threat Protection
- Anti-Malware
- Anti-Spam
- Anti-Virus
- Audit, Analysis and Compliance
- Breach Detection
- Content Filtering
- Data Destruction
- Data Loss Prevention
- Data Recovery
- Database Activity Monitoring
- Device Control
- Digital rights management (DRM)
Cisco Quickvpn Client Download
- Email Encryption
- End-user awareness and training
- Endpoint Detection and Response
- Endpoint Protection Platform
- File Access Auditing
- File Encryption
- Identity Management
- Intrusion Detection and Prevention (IDS/IPS)
- Mobile Forensics
- Network Access Control
- Network Access Control
- Network Security, Firewall and Packet Analyzers
- Password Management
- Patch Management
- Penetration Testing
- Physical Security
- Proximity Readers
- Public Key Infrastructure (PKI)
- SIEM, Log Management
- Single Sign-on
- Threat Protection
- Unified Threat Management (UTM)
- User Monitoring
- Virtual Private Network (VPN)
- Virtual Private Network (VPN)
- Vulnerability Scanners
- eDiscovery